Cloud Security Services
Importance of Cloud Security
Cloud security is a critical factor for businesses to effectively contain the flow of sensitive information and secure business data; in addition, it ensures business compliance with a swarm of regulations pertaining to data security and confines access to confidential data from any unauthorized sources. Nowadays, most of the organizations shifted towards cloud-based infrastructures; however, partnering with a reliable cloud security services provider such as Strategy Tech is essential in any dummy text cloud environment since it helps to mitigate risks.
Our Cloud Security Solutions
- Cloud Security Assessment: Perform stringent evaluations proactively to pinpoint the exposure and weak spots found in your cloud networks.
- Cloud Security Architecture Design: Create solid security structures with a unique cloud service in mind (for example, AWS, Azure, Google Cloud) robust to risks.
- Identity and Access Management (IAM): Implementing IAM solutions will ensure that cloud environments have a control over managing user access, authenticating users, and authorizing the kind of actions that users can perform.
- Data Encryption and Key Management: Implement data at rest and during transmission encryption, as well as manage the keys of encryption in a secure way.
- Cloud Security Monitoring and Incident Response: Cloud security environments have to be monitored continuously for any security threats and respond immediately to any incidents.
- Cloud Compliance and Governance: Help cloud compliance specifications (e.g., GDPR, HIPAA) and define government structures for cloud security.
Cloud Security Services
Our Cloud Security services include:

Cloud Security Assessment & Gap Analysis
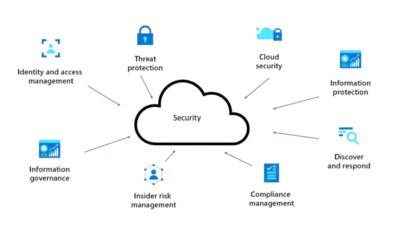
Architecture Design & Implementation

Data Encryption

Cloud Security Monitoring
Why Choose Us for Cloud Security Services
Engaging Strategy Tech for the cloud security services helps you leverage a group of certified experts with professional competence in securing cloud ecosystems. We provide unique services, designed to suit the particular security and compliance needs of your organization. Our proactive approach is through monitoring the security posture of your cloud continuously with assessment and identification of risks in real time. We adopt a vendor-agnostic approach and work with different cloud providers and technologies, which enables customers to have well-compatible and flexible cloud security solutions. Get comprehensive cloud platform protection services from [Your Company Name]. Get in touch with us now to arrange for a consultation and improve your business’ cloud security. Join us in our effort to secure your critical cloud assets.
FAQs About Cloud Security Services
Cloud security services are solutions which ensure that information, applications, and infrastructure in a cloud environment remain protected. Strategy Tech in Dallas, Texas provides total solutions that help prevent attacks on your cloud property.
- Data Encryption: Encountering how to protect data while being stored in databases and when moving across the network.
- Identity and Access Management (IAM): How to make certain the cloud resources can only be accessed by warranted users.
- Network Security: Procedures such as firewall and virtual private network accesses to the network.
- Compliance Management: The availability of some cloud services that do not meet regulatory and compliance requirements.
- Threat Detection and Response: Implementing systems that can identify and counter threats as and when they emerge.
- Preventive Controls: MIS appropriate security measures that protect systems from security breaches like firewalls and IAM.
- Detective Controls: Technologies to identify security threats, incident handling solutions, such as Intrusion Detection systems (IDS) etc.
- Corrective Controls: About the backup and disaster recovery measures which can be applied to help restore the systems and data after getting infected with the virus.
An example of cloud security is enforcing the multi-factor authentication policy (MFA) for access to cloud apps. This provides an increased level of security by asking users to prove identity in at least two ways.
Cloud security is used by enterprises and across industries and spheres, including financial, healthcare, retail, and governmental organizations, to safeguard their cloud landscapes and guarantee data integrity and compliance.
Cloud security can be attained through proper IAM policies adoption, data encryption, firewall, updated software, security audits, and scrutiny on any suspicious activities. This is how the correct usage of Strategy Tech can assist in protecting your cloud environment.
Different cloud services provide good security measures to guarantee the protection of its users’ data but the best one will be dependent on the service that the client requires. Amazon Web Services, Microsoft Azure and Google Cloud are considered comprehensive trusted security solutions. Read on and Strategy Tech will be able to assist you in deciding on the best clouds suited for your security needs.
Inadequate security measures remain the primary challenge when it comes to cloud security as people continue to misconfigure security settings, create easy-to-guess passwords, and fall for phishing scams, among other behaviors. Other vital threats include data breaches, insider threats, and insecure API.
There are many risks associated with cloud computing such as data leakages, lack of full control over data, non-compliance with legal requirements, availability issues with cloud service providers and cyber criminals attacks. These risks are however manageable through well rounded cloud security measures.
Cloud security entails using prevention, detection, and mitigation strategies to ensure the safety of the information technology infrastructure. This comprises of cryptology, identification and authentication, networking security, surveillance and detection, along with handling of incidents affecting cloud resources.
Cloud security is more precise in its sphere of concern, with the goal of safeguarding cloud spaces and resources, whereas cyber security involves a set of measures for ensuring the protection of any computing infrastructure, including both cloud and traditional premise-based systems.
Microsoft Azure cloud security can therefore be defined as the set of security solutions that are implemented and available in the Azure cloud for the purpose of protecting cloud based services and data. This entails Azure Security Center, Azure Active directory, Azure Encryption, and Azure compliance. In this article, Strategy Tech will be informing you of how you can protect your Azure cloud environment.

