SecOps Solutions
Importance of SecOps
SecOps Solutions offered by Strategy Tech
At Strategy Tech , we offer a comprehensive range of SecOps solutions tailored to address your unique security challenges:
- Security Assessment and Strategy Development: Evaluating systems for their susceptibility, and ascribing a personalized SecOps approach through this procedure.
- Continuous Monitoring and Threat Detection: Utilizing complex security monitoring mechanism testing and interactiveness with threat in general in real-time.
- Incident Response and Forensics: Designing the incident response procedures and running the forensic research are the best methods to control the influence of data breaches on the organization.
- Security Automation and Orchestration: Deriving the typologies out of the automation tools that will allow the security team to respond with speeds and improves their efficiency.
- Compliance and Governance: Establishing the industry norms and government regulations compliance could be achieved via a successful governance model.
SecOps Services
Our comprehensive SecOps services include:
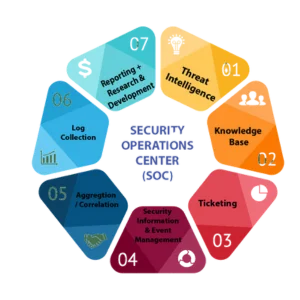
Security Operations Center (SOC) as a Service
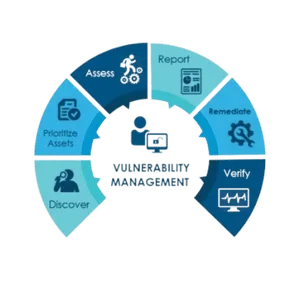
Vulnerability Management
Security Awareness Training
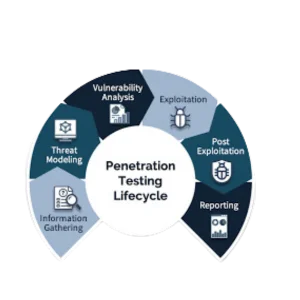
Penetration Testing and Ethical Hacking
Why Choose Strategy Tech
FAQs About SecOps Solutions
Security Operations or commonly known as SecOps refers to the method of managing and operating an organization’s physical and digital security. It is a shift towards how the IT security and operations group can work together for better security as well as service delivery.
The goals of SecOps are to strengthen the security, optimise the handling of security incidents, minimise the consequences of security incidents, maintain constant vigilance and compliance, as well as common goal of bridging the gap between security and operation departments.
SecOps is a sub-process of IT where security procedures remain active during operation to ensure protective measures, while DevOps is a software delivery model that guides enhanced communication between computer program developers and operational teams.
No; SOC stands for Security Operation Center which is a specific team responsible for security operations while SecOps stands for Security Operations which is a discipline of working security into the IT operations and often embraces SOC.
DevSecOps tools are an extension of the DevOps process that bring security into the integration. Some of the best tools are Jenkins with security plugins, GitLab CI/CD with built-in security scanning tools, SonarQube, docker security scanning, twistlock, and Checkmarx.
A SecOps analyst is an individual who keeps track of Security event and incident management, handles incidents, interacts with IT operations for integration of security measures, performs assessments for possible vulnerabilities and enforces security standards.
A SecOps module involves various tools, processes, and practices that are incorporated into an organization’s IT environment to boost security, such as threat and vulnerability identification, incident handling procedures, and real-time assessments.
The benefits delivered by SecOps include increased security, quick problem solving in terms of security incidences, sound compliance, better cooperation between the security and operation departments, and ongoing security assessment and safeguarding.
These include the enforcement of security practices into the IT operations through monitoring, constant alerting, assured automatic responses for various incidents, checkups of various vulnerabilities, and active cooperation between the security as well as operations departments in order to put into practice security measures.
SecOps in Azure includes Azure Security Center for live monitoring and threat protection, Azure Sentinel, for SIEM, and Azure Policy for enforcing compliance rules, security application in Azure DevOps pipeline, and Azure resources security.
SecDevOps is the practice of building security into the DevOps process from design through deployment, where security is examined continuously, weak points are acknowledged, threats are mitigated, teams work collaboratively to secure applications, and organizations become more secure and compliant.

